I started work on sysbox again recently, adding a couple of simple utilities. (The whole project is a small collection of utilities, distributed as a single binary to ease installation.)
Imagine you want to run a command for every line of STDIN, here's a good example:
$ cat input | sysbox exec-stdin "youtube-dl {}"
Here you see for every (non-empty) line of input read from STDIN the command "youtube-dl" has been executed. "{}" gets expanded to the complete line read. You can also access individual fields, kinda like awk.
(Yes youtube-dl can read a list of URLs from a file, this is an example!)
Another example, run groups for every local user:
$ cat /etc/passwd | sysbox exec-stdin --split=: groups {1}
Here you see we have split the input-lines read from STDIN by the : character, instead of by whitespace, and we've accessed the first field via "{1}". This is certainly easier for scripting than using a bash loop.
On the topic of bash; command-completion for each subcommand, and their arguments, is now present:
$ source <(sysbox bash-completion)
And I've added a text-based UI for selecting files. You can also execute a command, against the selected file:
$ sysbox choose-file -exec "xine {}" /srv/tv
This is what that looks like:
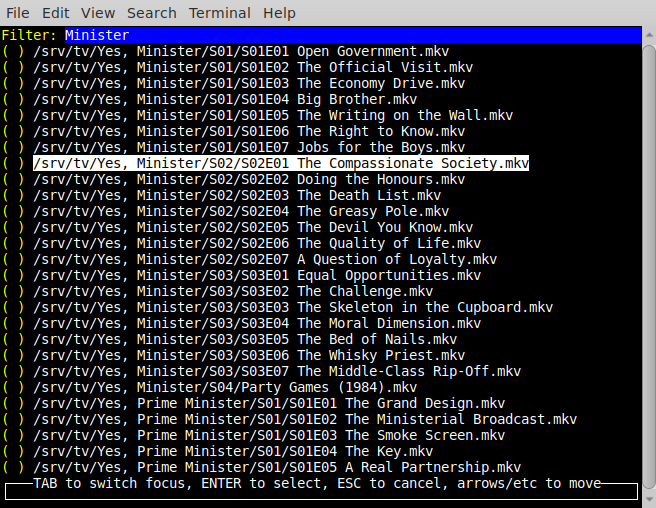
You'll see:
- A text-box for filtering the list.
- A list which can be scrolled up/down/etc.
- A brief bit of help information in the footer.
As well as choosing files, you can also select from lines read via STDIN, and you can filter the command in the same way as before. (i.e. "{}" is the selected item.)
Other commands received updates, so the calculator now allows storing results in variables:
$ sysbox calc
calc> let a = 3
3
calc> a / 9 * 3
1
calc> 1 + 2 * a
7
calc> 1.2 + 3.4
4.600000
Tags: golang, scripting, sysadmin, sysbox 2 comments